In case you’re a state-sponsored hacker siphoning data from selected computer systems, the very last thing you need is for somebody to find your command-and-control server and shut it down, finishing your capacity to communicate with contaminated machines and steal data.
The Russian-speaking spy gang often known as Turla have discovered a solution to this—hacking the satellite IP addresses of reliable customers to use them to steal from infected systems in a method that hides their command server. Researchers at Kaspersky Lab have found proof that the Turla gang has been utilizing the covert approach since, at the very least 2007.
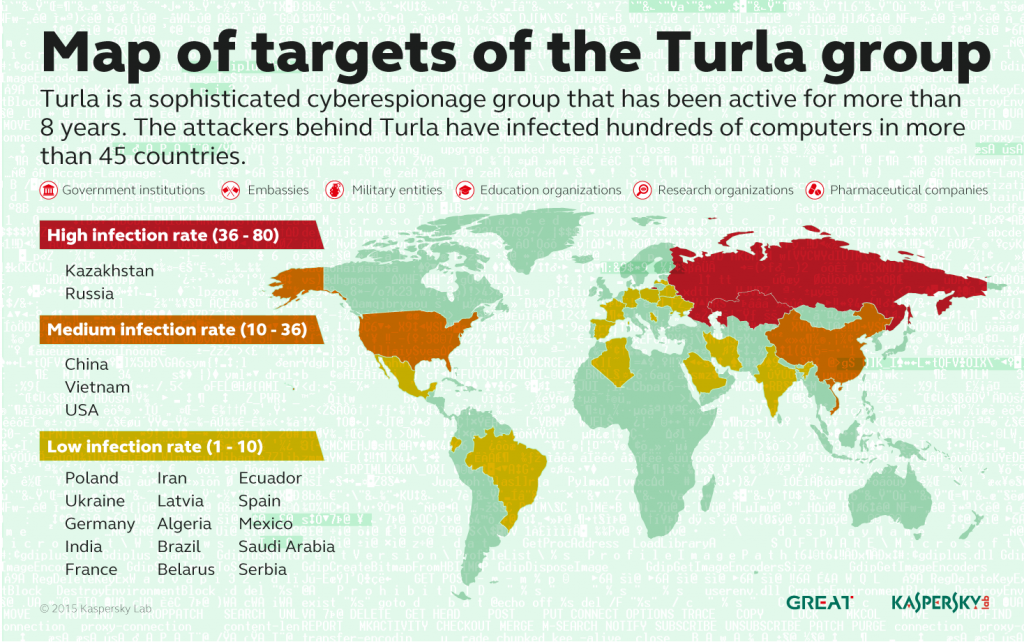
Turla is a sophisticated cyber-espionage group, believed to be sponsored by the Russian government, that has for more than a decade targeted government agencies, embassies, and militaries in more than forty nations, including but not limited to Kazakhstan, China, Vietnam, and the USA, however with a particular emphasis on countries in the former Eastern Bloc. The Turla gang uses various strategies to infect systems and steal information, but for some of its most high-profile targets, the group seems to use a satellite–based communication method to assist in concealing the location of their command servers, according to Kaspersky researchers.
“[This technique] essentially makes it impossible for someone to shut down or see their command servers,” Tanase says. “No matter how many levels of proxies you use to hide your server, investigators who are persistent enough can reach the final IP address. It’s just a matter of time until you get discovered. However by using this satellite link, it’s almost impossible to get discovered.”
How It Works
 One of the most widespread and least costly type of satellite connectivity is downstream-only, which individuals will typically use for faster downloads, since satellite connections tend to provide larger bandwidth than another connection methods. Traffic coming out of the person’s pc will go through a dial-up or other connection, whereas traffic coming in goes via the satellite connection. As a result of this satellite communication isn’t encrypted, hackers can point an antenna at the traffic to intercept the data or, in the case of the Turla hackers, determine the IP address of a authentic satellite users to be able to hijack it.
One of the most widespread and least costly type of satellite connectivity is downstream-only, which individuals will typically use for faster downloads, since satellite connections tend to provide larger bandwidth than another connection methods. Traffic coming out of the person’s pc will go through a dial-up or other connection, whereas traffic coming in goes via the satellite connection. As a result of this satellite communication isn’t encrypted, hackers can point an antenna at the traffic to intercept the data or, in the case of the Turla hackers, determine the IP address of a authentic satellite users to be able to hijack it.
Such vulnerabilities in the satellite system were made public in 2009 (.pdf) and 2010 (.pdf) in separate presentations at the Black Hat security convention. However the Turla hackers appear to have been utilizing the vulnerabilities to hijack satellite connections since at least 2007. Kaspersky researchers found a sample of their malware that appears to have been compiled in 2007. The malware sample contained two hard coded IP addresses for communicating with a command server—one of them an address that belonged to a German satellite ISP.
The method isn’t reliable for long-term exfiltration of data, since these satellite internet connections are one-way and can be very unreliable. The attacker will also lose the satellite connection once the innocent user whose IP address he has hijacked goes offline. “This is why we believe they only use it on the most high-profile targets,” Tanase says, “when anonymity is essential. We don’t see them using it all the time.”
The researchers saw the Turla hackers communicating through satellite connections around the world, but most of their activity concentrated in two specific regions. “They seem to have a preference for using IP ranges assigned to providers in the Middle East and African regions–the Congo, Nigeria, Lebanon, Somalia, and the United Arab Emirates,” says Tanase.
All the hijacking requires is a satellite dish, some cable, and a satellite modem, which costs around a thousand dollars.