For the last couple of weeks Sucuri have been tracking a new Malware threat that has gained significant traction over the past forty eight-seventy two hours. The malware they call the “Active VisitorTracker Campaign” is fairly easy to identify because of very particular “visitorTracker_isMob” code being used.
As of the 18th September 2015, slightly over 6 million web sites now contaminated, with over 5 million of these infections occurring within the last 48 hours. The chart created by Sucuri shows the rate of infections below:
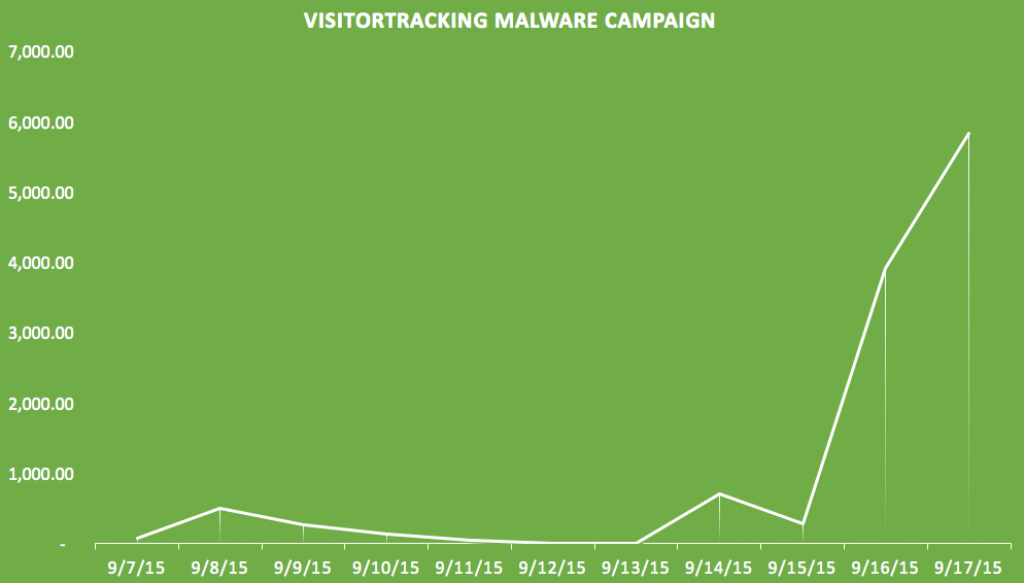
What does the Active VisitorTracker Malware do?
Based on Sucuri, the final objective of the infection is to redirect the visitors of the website to a Nuclear Exploit Kit landing pages, which may in turn use numerous methods to infect the physical computers of these visitors. Some examples of the strategies used include infecting the visitors computer utilizing Flash, Silverlight, PDF, and Internet Explorer to install malware or ransomware.
For more detailed \ technical article on the Nuclear Exploit Kit click here.
The exploit works by inserting the following code in to your web site:
-
function visitorTracker_isMob( ) var ua = window.navigator.userAgent.toLowerCase(); if(/(androidmobile|avantgo|bada\/|blackberry|blazer|compal|elaine|fennec|hiptop|iemobile|ip(hone|od)|iris|kindle|lge |maemo|mi..|v400|v750|veri|vi(rg|te)|vk(40|5[0-3]|\-v)|vm40|voda|vulc .. |vx(52|53|60|61|70|80|81|83|85|98)|w3c(\-| )|webc|whit|wi(g |nc|nw)|wmlb|wonu|x700|yas\-|your|zeto|zte\-/i.test(ua.substr(0,4))) return true; return false; /* .. visitorTracker .. */ /*
This code will then force the visitors web page to load an iframe from one of many Nuclear Exploit Kit landing pages which then infects the visitors computer system.
An example of the exploit in action has been noted by Jerome Segura from MalwareBytes showing an infection on a web site owned by a big security provider (Coverity):
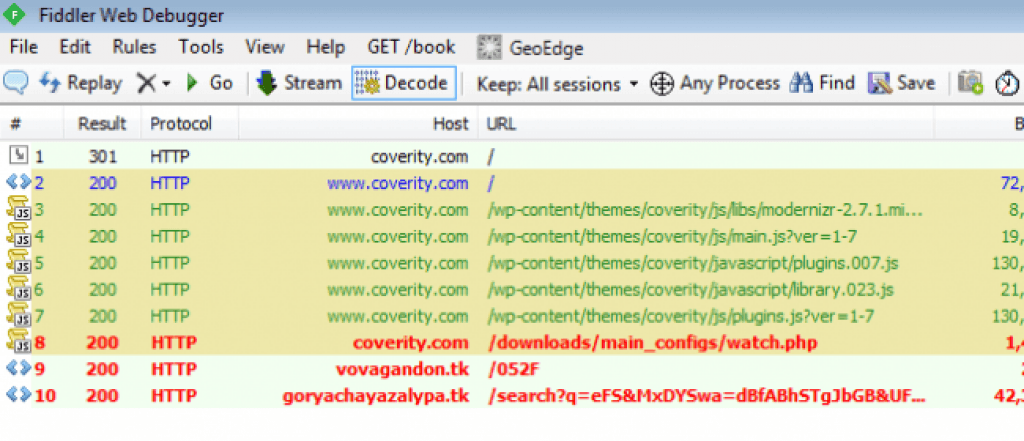
However they aren’t the only major security firm affected by this exploit.
Sucuri itself is infected by this Malware [Update: FALSE POSTIVE]
What concerns us very deeply is that Sucuri’s own labs (dot) sucuri (dot) net (don’t visit it – we are going to update when it’s secure) website is contaminated by this very malware. Their main blog post on this very Malware links to an article on that sub-domain with additional information on the exploit.
For a security firm, it’s quite serious that they’re really directing you to click a link to a contaminated page, and we immediately reached out to them via their support site and via their live chat to let them know. At the present time we do not have a reply/see any action has been taken.
We were first alerted to the fact their website was infected by Norton Antivirus as shown beneath:
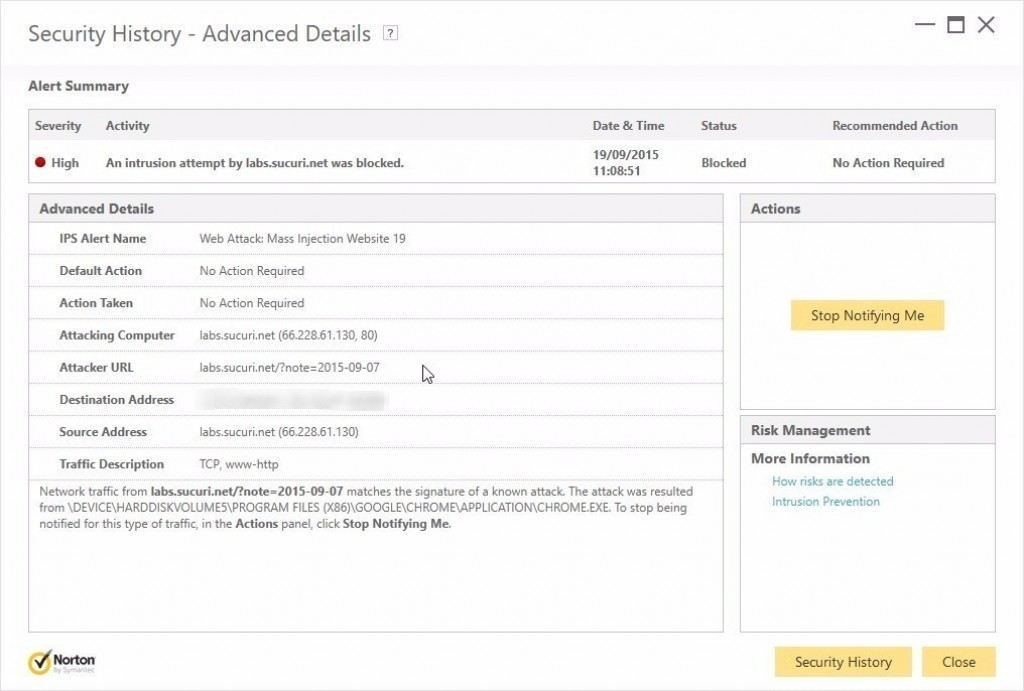
We then followed this up by using Sucuri’s own Site Scanner Tool, which confirmed that malicious code was detected, and that the code of the infection contained the following:
-
if(visitorTracker_isMob())
while also referring to their Malware entry: MW:JS:GEN2 (we will link to the page once we confirm the malware has been eliminated).
You can see a screenshot of their infection below:
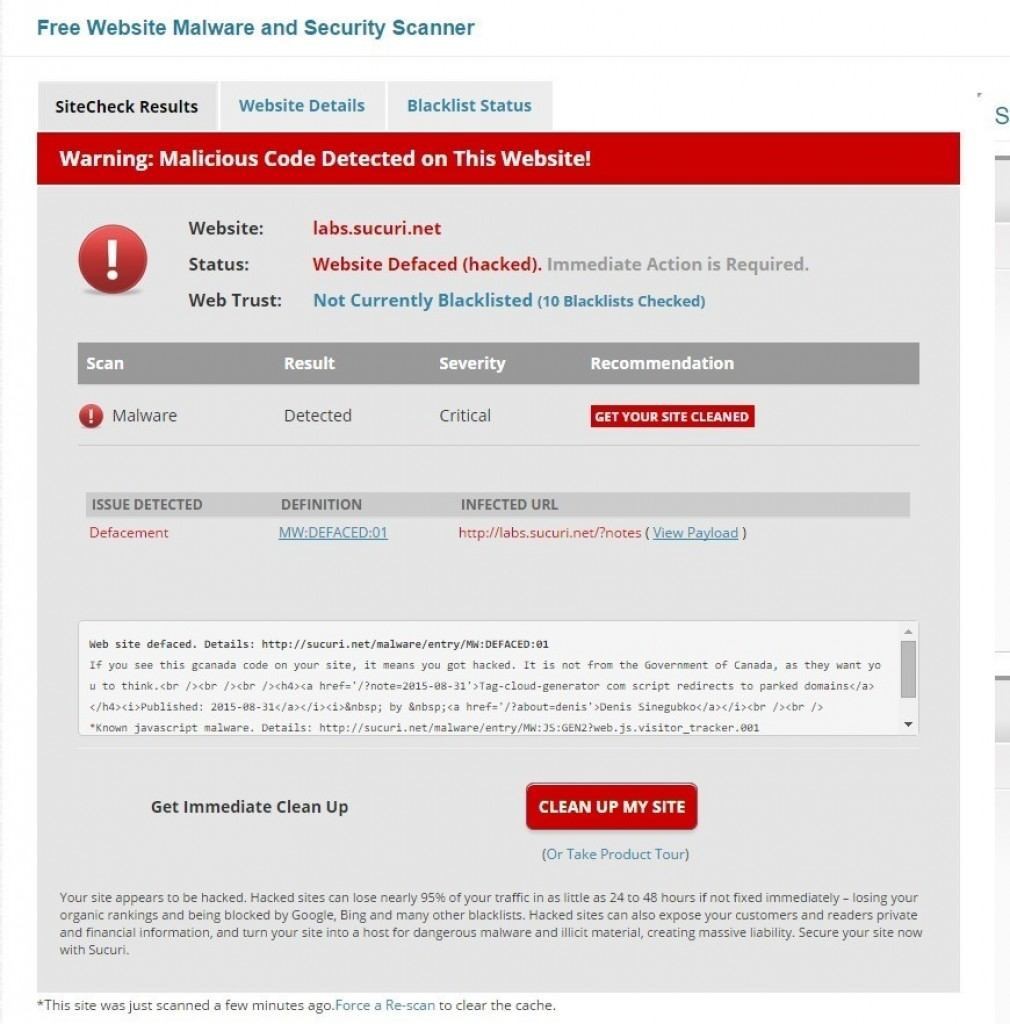
Obviously, it is extremely serious that a web site people use to find out extra info on this infection is in turn responsible for spreading the infection itself.
UPDATE:
SUCURI REPONDED: “Indeed, since we publish details about attacks and malicious code on labs.sucuri.net, this can sometimes be flagged in SiteCheck. Not a big deal, though — you can see it’s alerting about a blog post that actually discusses the malware in question.
THE CEO of SUCURI then Added:
Yes, we flagged ourselves. and it caused others, like Norton to flag us as well.. these however are false positives. We have direct lines of communication with many vendors
Many of Infected Sites already blacklisted by Google
The seriousness of this Malware cannot be understated. Not only are you opening up your Guests computers to malware/ransomware, but Google appears to be very quickly blacklisting any site affected by this exploit.
Based on Sucuri, 17% of all websites they’ve found with the exploit are already blacklisted by Google and other popular blacklists.
How to test if your Site is infected with the VisitorTracker Malware?
The simplest method to check if your website is contaminated is to use this free tool by Sucuri. (This is safe to use)
How can you protect yourself as a website visitor?
While we haven’t checked all firewalls or antivirus programs but we are able to confirm that MalwareBytes and Norton successfully prevented us from visiting a website infected with this malware.
Here is Mr Tony Perez’s (CEO of Sucuri) full response. We (GadgTecs) apologize deeply for the confusion.
Thanks for sharing our information, but I did want to let you know it is a bit misleading. We are not and have not been compromised by this infection.
As an organization we invest heavily in research, specifically the public disclosure of that research to keep communities such as this one informed. This sometimes requires us to release snippets of malware variants, such as was the case here.
Yes, we flagged ourselves.. 🙁 and it caused others, like Norton to flag us as well.. these however are false positives. We have direct lines of communication with many vendors
If you have any other questions, please let me know I’d be happy to expand on the subject if required.
Tony Perez
Sucuri – CEO














































[…] Source: A Malware Called Active VisitorTracker Campaign Infecting WordPress Websites […]
[…] Source: A Malware ‘Active VisitorTracker’ Infecting WordPress Sites […]
[…] Source: A Malware ‘Active VisitorTracker’ Infecting WordPress Sites […]